2 minutes
OpenShift: Managing Users with the HTPasswd Identity Provider
Managing user credentials with the HTPasswd Identity Provider requires creating a temporary htpasswd file, making changes to the file and applying these changes to the secret.
Create an HTPasswd File
Create or update the HTPasswd file
```
$ htpasswd -c -B -b htpasswd user password
```
Add or update credential
```
$ htpasswd -b htpasswd user password
```
Delete credential
```
$ htpasswd -D htpasswd user
```
Create the HTPasswd Secret
To use the HTPasswd provider, you must create a secret that contains the HTPasswd file data. In the following example, the secret is named htp-secret.
$ oc create secret generic htp-secret --from-file htpasswd=/home/user/htpasswd -n openshift-config
Updating the HTPasswd Secret
The secret must be updated after adding, changing, or deleting users. To update the secret named htp-secret, run the following command:
$ oc create secret generic htpass-secret --from-file htpasswd=/path/to/your/file --dry-run -o yaml | oc replace -n openshift-config -f -
Extracting Secret Data
Extract the secret data when adding or removing users.
$ oc extract secret/htp-secret -n openshift-config --to - > temp.htpasswd
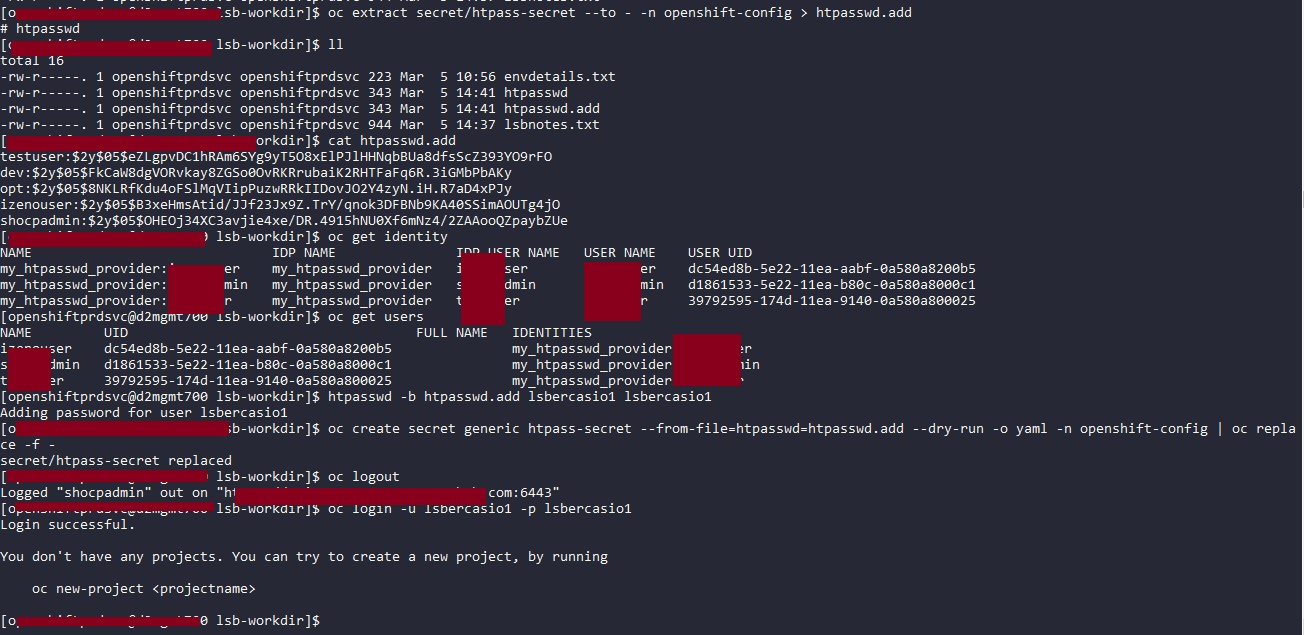
Resetting Password
Extract the secret data
$ oc extract secret/htpass-secret --to - -n openshift-config > htpasswd.reset
Modify the user password
$ htpasswd /home/openshiftprdsvc/htpasswd.reset eimuser
New password:
Re-type new password:
Updating password for user eimuser
Commit the updated secret data
$ oc create secret generic htpass-secret --from-file=htpasswd=htpasswd.reset --dry-run -o yaml -n openshift-config | oc replace -f -
Assigning Administrative Privileges
Only do this when granting cluster-wide cluster-admin role to users and groups
$ oc adm policy add-cluster-role-to-user cluster-admin adminuser